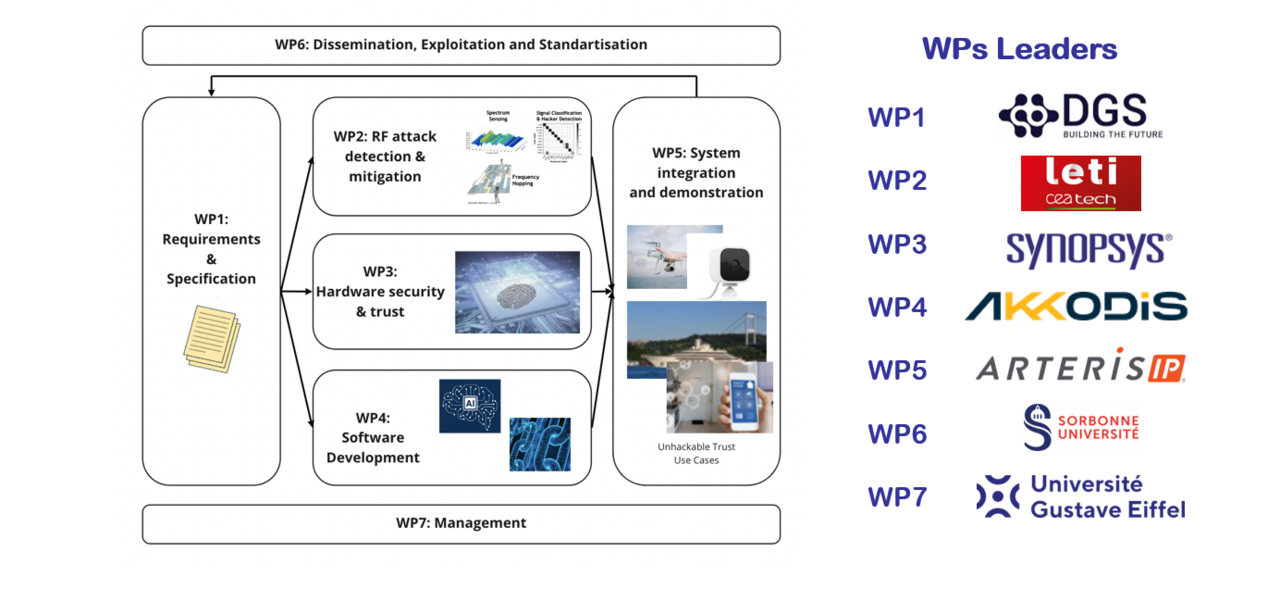
In WP1, the state of the art of the IC development and supply chain infrastructure and secure firmware update are analyzed and the main Supply IC actors are defined. The role of each actor in the supply chain is described together with the associated assets. The work is also to describe the attacker profiles. It aims also to compare possible threats to the unprotected system. Some identified threats are analyzed to determine the risk they pose to the supply chain and secure firmware update.
---------------------------------------------------------------------------------------------------
The main objective of the WP2 is to develop all the needed hardware IPs necessary for the RF attack detection and mitigation demonstrator. It starts by the selection and optimization of the overall architecture of the systems. Then, the building blocks have to be designed (RF sensing, Flexible Transceiver and PUF) and the AI hardware accelerator will be developed in a second step. Lastly, RF attack mitigation solutions concepts will be studied and finalized.
---------------------------------------------------------------------------------------------------
The WP3 uses the requirements of WP1 to define the hardware architecture of a security subsystem including a low-power processor and cryptographic extensions. The security subsystem handles the security sensitive operations of a device, without exposing the used cryptographic keys to the outside. For example, it handles the cryptographic operations used in security protocols for secure boot, authentication and data encryption. The security subsystem consists of a secure low-power processor that has several cryptographic extensions. The cryptographic keys that are needed for the cryptographic operations executed by the secure processor are generated and managed by a PUF (Physical Unclonable Function) based root-of trust. The PUF uses device-unique silicon properties to extract a cryptographic root key. None of these keys ever needs to be stored in non-volatile memory, so there are no keys at rest that an attacker can find. Keys are simply reconstructed on the fly from the PUF. A second use of the PUF is to serve as a public identity that can be used as part of the supply chain traceability and provenance mechanism. This requires a separate instance of the PUF with a dedicated interface for this purpose. It is required that the PUF has sufficiently good reliability and entropy properties, such that a full entropy root key can be extracted from it in a reliable and efficient manner. The security architecture around the PUF primitive and security processor needs to assure that the security subsystem has a dedicated and safe interface where its functions can be called without exposing any sensitive (side) information.
The objectives of WP3 are:
- The design of PUFs to realize root of trust and support other secure primitives.
- The design and implementation of a secure low-power processor (System-on-Chip) and crypto extensions (low-resources cryptographic primitive) that uses the PUF-based security primitives.
- The research and design of security vulnerability assessment methods and mitigation techniques.
- The Development of a hardware architecture for the security subsystem.
---------------------------------------------------------------------------------------------------
The WP4 aims to define the software architecture of the secure low-power processor including the extension, security feature, interoperability,and connection to the blockchain. The preliminary works has to provide inputs to define the low and high level security architectures for the libraries and the APIs layers, while the deliverable D1.4 guidelines will be transposed into a system security design pattern involving the Cloud and Blockchain integration.
The objectives of WP4 are:
- The definition of software blocks for cryptography and security services.
- The development of simulations or mocking to verify the functionality of the blocks.
- The optimizations of design metrics.
- The creation of a layered architecture.
- The definition of an API for cryptographics services (IC management, IC authentication).
- The development of a neural network-based attack detection system.
- The construction of a Deep Neural Network for attack recognition.
- The rule framework for counter measures.
---------------------------------------------------------------------------------------------------
The objective of the WP5 is to develop demonstrators and assess the advantage of embedded AI, secure and trusted supply chain, secure by design software application in wireless communications devices and systems over the state-of-the-art.
In a first step, we use the state-of-the-art method, based in IP-XACT standard, to describe the components to be assembled. Several integration scenarios will be studied. Those design intents may be configurable or parameterizable in order to facilitate design exploration. The meta-description in IP-XACT will be enlisted in situatable prototypes, described either in TLM languages (SystemC, System-Verilog) or in RTL to link the path to implementation.
The use of such virtual prototype, at metadata, TLM or RTL level, allow different validation and verification strategies and technics. This activity will help in IP integration, communication, HW/SW integration, performance analysis, etc.
This objective is translated into the following detailed objectives:
- Integrate HW design results of WP2 and WP3 in a single SoC
- Implementation of the SoC prototype: development, integration and tape-out
- Develop project prototypes and simulations based on modular hardware and software to bring AI into Cybersecurity with Edge/Cloud approaches
- Integrate and validate hardware and software components, both on client- and host-side, into the single prototype
- Demonstrate the project concepts in the relevant use cases