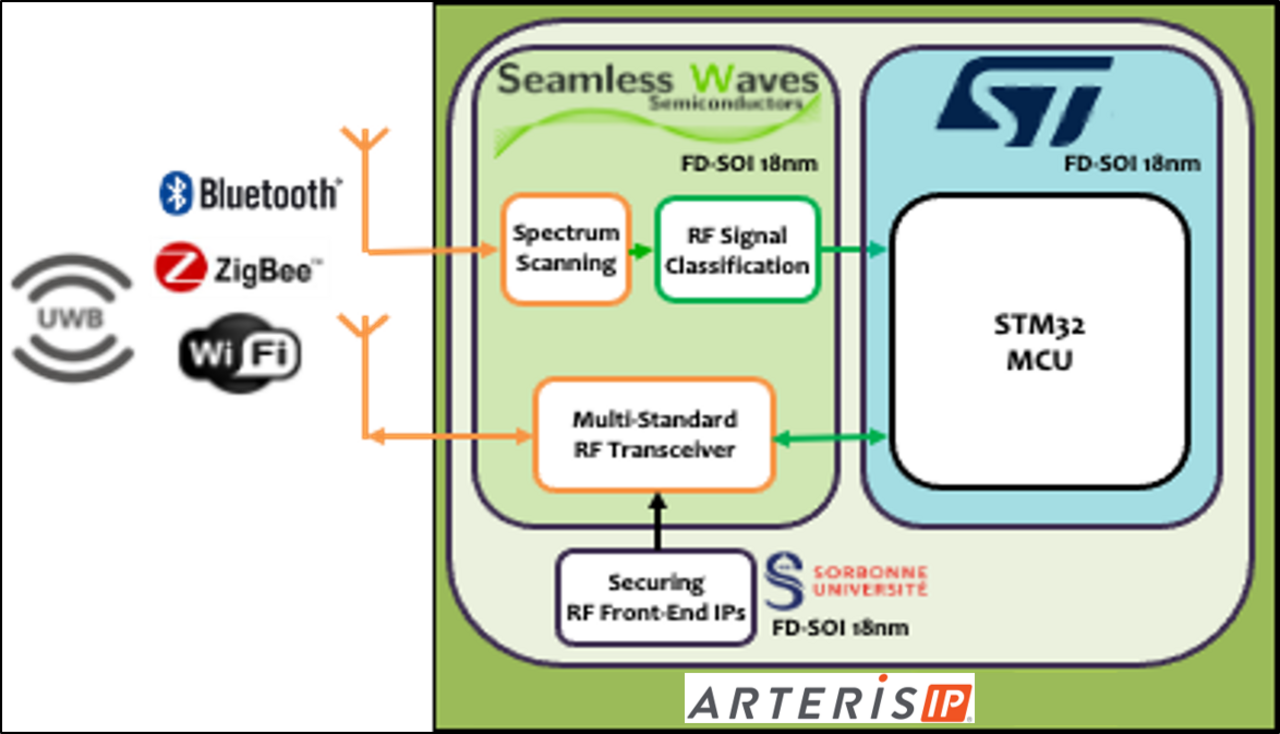
The STM32 Micro Controller Unit (MCU) is very popular with IoT applications. More than 2 billion chips have been sold in the last 5 years. Current versions of the STM32 can communicate using 2 different wireless communication standards Bluetooth Low Energy and Zigbee. Both are low data-rate standards operating in the 2.4 GHz ISM frequency band. In order to widen the use of the STM32 MCU to new IoT applications, it is necessary to add more wireless communication standards with higher data-rates.
Recently Seamless Waves proposed a new architecture based on a tunable RF Bandpass Sigma-Delta ADC. The advantage of this technique is that it combines the low power consumption of conventional RF transceivers with the flexibility of highly digitized architectures.
The ambition of this project is to design, fabricate and measure a chip containing a multi-standard transceiver suitable for the following standards: WiFi (2.4/5.0/6.0 GHz), UWB (3.5-8.0 GHz) and DECT NR+ (1.9 GHz) in addition to Bluetooth and Zigbee at 2.4 GHz.